Google
is a tool which helps in finding what one is looking for. Google operators are
the terms provided to us for making our search easy and refined. These
operators also termed as advanced Google operators provides the exact information.
It reduces the time of search by instantly providing the information as we
don’t have to move from one page to another one. These operators’ works as a
query.
The
basic syntax is->operator: term to be searched
Some
of these operators are enlisted below:
Intitle
e.g->intitle:hackingarticles
This
query will return the pages which include the term “hackingarticles”in it.
inurl
e.g->inurl:hackingarticles
This query will return the pages which includes the term hackingarticles
in its URL.
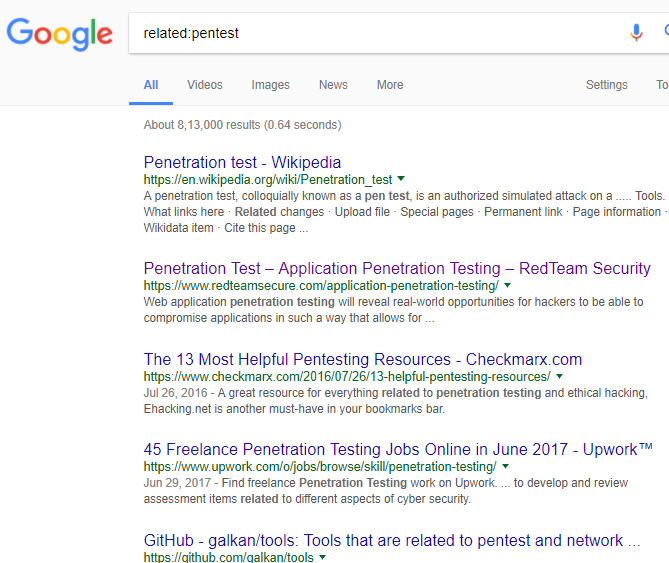
Related
e.g->related:pentest
It will provide the result related to our query i.e.pentest
Allintext
This operator will perform the task of locating a particular
string in the text of the page .
e.g->allintext:rajchandel
The above given query will return only those pages which
include the terms rajchandel in the text.
Filetype
e.g->www.kccitm.edu.in
filetype:pdf
This query searches
the file of the provided extension only. The above given query will search only
the pdf files present on the given site.
Cache
This operator will show the cached version of the webpage
instead of the current one. This operator is followed by the URL of the page of
which we want to have the cached version.
Define
This operator provides the definition of a term as a result.
e.g->define:pentest.
Link
This operator will
help you to search the pages which links to other pages. This operator is
provided a URL instead of a term to search.
e.g->link:www.kccitm.edu.in
Allintitle
This operator is slightly different from the intitle
operator.
In intitle operator there was no compulsion of the term in
the query to be present in the title whereas in allintitle operator this is
must for the term in the query to be present in the title.
e.g->allintitle:hackingarticles
ADVANTAGES:
1. These operators provides the exact results which we are
looking for.
2. There is no wastage of time as there is no redirecting
from one page to another.
3. There are different operators for every task to perform i.e.
Phonebook to obtain residential and business phone numbers and so on.
DISADVANTAGES
1. There are some
operators which do not mix with another in the same query, for e.g,
allintitle,allintext operators .
BASIC
GUIDELINES TO USE GOOGLE OPERATORS
1. There should be no
space between the operators, colon and the search as violating this rule will
not generate the desired result.
2. If the search term
is a phrase then there should be no space between the operator, colon as well
as the first quote of the phrase.
3. Some advanced
operators cannot be combined with others such as allintitle, allintext etc.
4. Boolean operators
and special characters such as ‘OR’ and ‘+’ can be used in the queries but they
should not be placed in the way of the colon.
HOW HACKERS USE GOOGLE OPERATORS
Everyone use google
but most of them don’t know to make use of google.
Google operators are very famous among hackers and they take
full benefit of it.
Sensitive information needed by hackers which are not easily
retrieved through common search can be produced by the help of google
operators.
If a hacker wants to retrieve a pdf file of a particular
site then he/she has to use the operator “Filetype” with the URL as well as the extension of the file.
A hacker can retrieve the site of the specified domain with
the help of the operator “site”. This operator is followed by the separating
colon and the domain name.
It’s an easy tool for a hacker to get the exact outcome in
just a click.
Thanks for reading the article. In next article we will be
discussing about more google dorks with web penetration testing.
Author: Shrishtee Suman is Technical
Writer in hacking Articles she is pursuing B. Tech in CS. Her interests are mainly in Web
Penetration testing and vulnerability research. Contact Here